In today's interconnected world, securely connect remote IoT P2P SSH Android has become a critical topic for businesses, developers, and users alike. The rise of Internet of Things (IoT) devices and the increasing need for remote access has created new challenges and opportunities in the realm of cybersecurity. Understanding how to establish secure connections between IoT devices using peer-to-peer (P2P) SSH on Android is essential for protecting sensitive data and ensuring network integrity.
As the number of IoT devices continues to grow exponentially, so does the risk of unauthorized access and cyberattacks. This article aims to provide a comprehensive guide on how to securely connect remote IoT devices using P2P SSH on Android, covering everything from the basics to advanced techniques. Whether you're a developer, IT professional, or simply an enthusiast, this guide will equip you with the knowledge and tools needed to safeguard your IoT ecosystem.
By the end of this article, you'll have a clear understanding of the importance of secure connections, the role of SSH in IoT security, and practical steps to implement P2P SSH on Android. Let's dive in and explore the world of secure IoT connectivity.
Read also:The Power And Efficiency Of Remote Access In Iot
Table of Contents
- Introduction to Remote IoT Connections
- Understanding SSH in IoT
- P2P SSH Overview
- Android SSH Clients
- Securely Connect Remote IoT Devices
- Best Practices for IoT Security
- Common Vulnerabilities and Threats
- Tools and Technologies
- Real-World Implementation Examples
- Future Trends in IoT Security
Introduction to Remote IoT Connections
Remote IoT connections are the backbone of modern smart systems, enabling devices to communicate and exchange data across vast distances. In this section, we will explore the basics of remote IoT connections and why security is paramount.
Why Security Matters
IoT devices are often deployed in environments where they are exposed to various security threats. Without proper security measures, these devices can become entry points for malicious actors. Here are some reasons why security is crucial:
- Protection of sensitive data
- Prevention of unauthorized access
- Maintenance of system integrity
Understanding SSH in IoT
SSH (Secure Shell) is a cryptographic protocol designed to provide secure communication over unsecured networks. In the context of IoT, SSH plays a vital role in ensuring that data transmitted between devices remains confidential and tamper-proof.
How SSH Works
SSH establishes a secure channel by encrypting data packets and authenticating both the client and server. This ensures that even if data is intercepted, it cannot be read or altered without the appropriate decryption keys.
P2P SSH Overview
Peer-to-peer (P2P) SSH allows IoT devices to communicate directly with each other without the need for a centralized server. This approach reduces latency and improves efficiency, making it ideal for applications requiring real-time data exchange.
Advantages of P2P SSH
- Reduced reliance on intermediaries
- Improved performance
- Enhanced security through direct connections
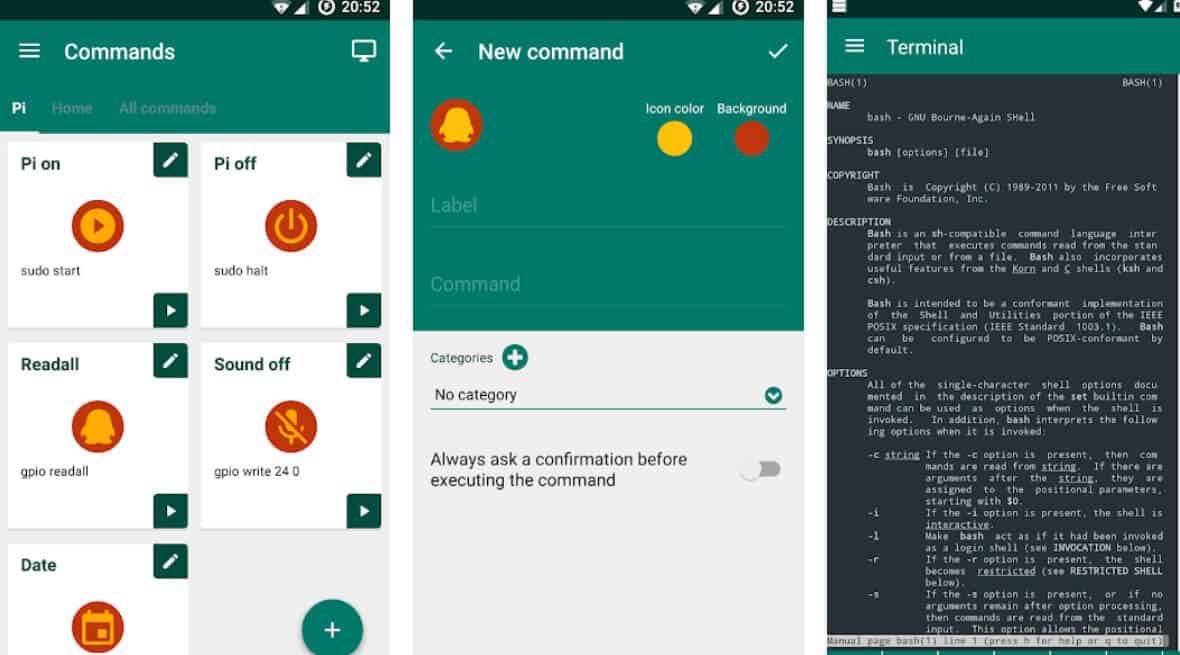
Android SSH Clients
Android devices can be used to establish SSH connections with IoT devices. There are several SSH client applications available on the Google Play Store that offer robust features for managing remote connections.
Read also:Claude Blue Baker A Comprehensive Guide To His Life Career And Legacy
Popular Android SSH Clients
- Termius
- ConnectBot
- ServerAuditor
Securely Connect Remote IoT Devices
Establishing a secure connection between remote IoT devices requires careful planning and execution. Below are the steps to securely connect remote IoT devices using P2P SSH on Android:
Step-by-Step Guide
- Install an SSH client on your Android device
- Configure the SSH server on your IoT device
- Generate SSH keys for authentication
- Establish a P2P connection between devices
Best Practices for IoT Security
To ensure the security of your IoT ecosystem, it's essential to follow best practices. Here are some recommendations:
Key Recommendations
- Use strong, unique passwords
- Enable two-factor authentication (2FA)
- Regularly update firmware and software
- Monitor network activity for suspicious behavior
Common Vulnerabilities and Threats
IoT devices are susceptible to various vulnerabilities and threats. Understanding these risks is the first step in mitigating them.
Types of Threats
- DDoS attacks
- Malware infections
- Data breaches
Tools and Technologies
Several tools and technologies can help enhance the security of IoT devices. From intrusion detection systems to encryption protocols, these solutions provide an additional layer of protection.
Recommended Tools
- Wireshark
- OpenSSH
- Nmap
Real-World Implementation Examples
Real-world examples demonstrate the practical applications of securely connecting remote IoT devices using P2P SSH on Android. From smart home systems to industrial automation, the possibilities are endless.
Case Study: Smart Home Automation
In this case study, we explore how a homeowner used P2P SSH to remotely control and monitor their smart home devices, ensuring both convenience and security.
Future Trends in IoT Security
The future of IoT security is shaped by emerging technologies and evolving threats. As we move forward, it's crucial to stay informed about the latest trends and innovations in the field.
Emerging Technologies
- Quantum cryptography
- AI-driven security solutions
- Blockchain for secure transactions
Conclusion
In conclusion, securely connecting remote IoT devices using P2P SSH on Android is a critical aspect of modern cybersecurity. By following the guidelines and best practices outlined in this article, you can protect your IoT ecosystem from potential threats and ensure seamless connectivity.
We encourage you to take action by implementing these security measures in your own projects. Feel free to leave a comment or share this article with others who may find it valuable. Additionally, explore our other resources for more insights into IoT security and related topics.